WordPress Bug Bounty
Comprehensive Guide
Want to break into ethical hacking or sharpen your web security skills? This comprehensive WordPress bug bounty guide walks you through everything you need to know to start hunting real vulnerabilities in WordPress plugins and themes, and get rewarded for it.
Learn how to responsibly disclose bugs, earn official CVE credits, and get paid through leading platforms like Wordfence and Patchstack.
You’ll also get hands-on practice by reproducing a real high-severity XSS vulnerability (CVE-2024-6770) in a safe, sandboxed environment.
Table of Contents
What Is WordPress Bug Bounty?
The WordPress bug bounty rewards researchers for finding vulnerabilities in plugins, themes, and WordPress core. With over 60,000 plugins—many built by junior developers—there’s a vast landscape of bugs waiting to be discovered.
While simple bugs like basic XSS or CSRF might not yield large payouts, they offer critical learning opportunities. Reporting bugs responsibly builds your resume, earns CVEs, and demonstrates real-world security skills.
This guide covers everything you need to start: setting up your local testing environment, identifying vulnerabilities, reporting responsibly, and earning payouts through top programs like Wordfence and Patchstack.
Benefit to the WordPress Ecosystem
Bug bounty programs do more than reward individual researchers — they actively improve the security of the entire WordPress ecosystem which powers over 43% of all websites in the world.
Newer volunteers often start by probing small or recently released plugins, which makes it easier to learn, while experienced players focus on widely used or technically complex ones.
Therefore actively testing the entire WordPress attack surface.
When a vulnerability is found, the researcher is rewarded — sometimes with a CVE ID, sometimes with cash payouts, depending on severity and scope. These findings are then responsibly disclosed to the plugin developer, who often releases a security patch within days.
This feedback loop creates a ripple effect:
-
Developers improve their coding practices.
-
Users receive safer updates.
-
Researchers build real-world skills and reputations.
-
The entire ecosystem becomes harder to exploit.
Bug bounty programs make WordPress stronger — not through top-down enforcement, but through collaborative, community-driven security.
💡 It’s a modern, decentralized approach — almost an ideal system by design, where everyone benefits and the web becomes safer through open collaboration.
What Should You Know to Start?
Nothing if you are ready to learn. But it would be nice to know…
-
WordPress + Plugins: Understand how plugins extend WordPress functionality. Most vulnerabilities exist in third-party plugins, making them the ideal place to begin.
-
XSS (Cross-Site Scripting): One of the most common plugin flaws. Learn how malicious scripts get injected and executed through unsanitized input fields. (See: CVE-2024-6770 for an example.)
-
Automation Basics: Familiarity with Bash, Python, or PowerShell can help you write scripts to test at scale and speed up your workflow.
-
Burp Suite: A must-have tool for intercepting HTTP traffic and manipulating requests. Ideal for testing forms, AJAX endpoints, and plugin functionality.
-
Docker or Local Hosting: Set up WordPress safely using Docker or XAMPP so you can test in a sandboxed environment without risk.
WordPress Bug Bounty Payouts
Wordfence vs. Patchstack
Wordfence
Focus: High-impact vulnerabilities in WordPress plugins/themes with 50,000+ active installs.
Payout Structure
-
RCE / Privilege Escalation / Arbitrary File Upload (1M+ installs):
$1,600 – $3,000+ – These are the highest severity bugs, allowing remote code execution or full site compromise. -
SQL Injection / Arbitrary File Deletion: $800 – $1,200 – These flaws can lead to data breaches or full site data loss.
-
XSS / CSRF (1M+ installs): $80 – $320 – Considered lower risk but still impactful, especially on highly installed plugins.
Scope
-
Only WordPress plugins and themes with 50,000+ active installs are eligible.
-
Vulnerabilities must affect the latest version at time of submission.
Perks
-
Public researcher credit: Recognition on the Wordfence blog and site.
-
CVE assignment: Official CVE ID for qualifying vulnerabilities.
-
Guaranteed payouts: All valid reports get paid, no leaderboard or lottery system.
-
Well-documented triage process and quick feedback.
Latest Data and Payouts: Wordfence Bug Bounty
Patchstack
Focus: A broader bounty program covering all WordPress plugins and themes, regardless of install count.
Payout Structure
-
Monthly total prize pool: $8,850+
-
Top prize each month: $2,000
-
Per-report payouts:
Range from $300 to $14,400+, depending on:-
Plugin install base
-
Vulnerability impact (RCE, XSS, SQLi, etc.)
-
Uniqueness and difficulty of the exploit
-
Scope
-
All plugins/themes in the WordPress ecosystem are eligible.
-
Rewards scale with:
-
Active install count (e.g. 10k vs. 1M)
-
Technical impact (e.g. RCE > CSRF)
-
Perks
-
Monthly leaderboard: Compete with other researchers globally.
-
Public researcher profile: Showcase your contributions.
-
CVE assignment: Vulnerabilities get official tracking numbers.
-
Active community: Events, discussions, and internal collaboration.
-
Transparency reports: Patchstack publicly discloses fixed vulnerabilities.
Latest Data and Payouts: Patchstack Bug Bounty
Other WordPress Bug Bounty Vendors
Summary
Should You Start WordPress Bug Bounty Hunting?
🟢 Pros
-
Low Barrier to Entry
You don’t need elite hacking skills to get started. Many vulnerabilities are simple XSS or CSRF bugs.
-
Huge Attack Surface
60,000+ plugins = endless opportunities to find bugs, especially in poorly maintained or lesser-known plugins.
-
Earn While You Learn
Get paid to improve your skills, with bounties ranging from $80 to over $3,000 per vulnerability.
-
Recognized CVEs + Career Growth
Gain CVEs tied to your name, boosting your resume and credibility in cybersecurity job applications.
-
Remote-Friendly & Flexible
Hunt vulnerabilities from anywhere, on your own time.
🔴 Cons
-
Low Rewards for Basic Bugs
Simple XSS or CSRF issues may only pay $80–$300 unless they affect a popular plugin.
-
Time-Intensive
Testing plugins manually or setting up automation takes effort and persistence.
-
Duplicate Submissions Are Common
Someone may already have reported the vulnerability, disqualifying your submission.
-
Delayed Payouts
Some programs only pay once the vendor releases a patch, which can take weeks or months.
-
No Guarantee on Smaller Plugins
Wordfence only accepts plugins with 50k+ installs; Patchstack might not reward all low-severity issues unless they earn leaderboard points.
Top 10 WordPress Bug Bounty Tips for Beginners
Want to break into WordPress bug bounty hunting and actually start earning? Here are 10 practical tips for beginners looking to find plugin vulnerabilities, earn CVEs, and get paid.
1. Start with Small Vulnerable Plugins
Use intentionally vulnerable plugins or outdated versions to learn how real WordPress plugin vulnerabilities work. Practice with known bugs like CVE-2024-6770.
2. Master the Basics of WordPress Plugins
Understand how plugins are structured, where input/output happens, and what common attack surfaces exist (forms, AJAX, REST endpoints).
3. Learn to Detect XSS and CSRF First
Cross-Site Scripting and Cross-Site Request Forgery are the most common bugs in WordPress. They’re beginner-friendly and frequently found in plugin settings or contact forms.
4. Use a Local Testing Environment
Set up a WordPress bug bounty lab with Docker, Local WP, or XAMPP. Never test on live sites—use sandboxed environments.
5. Automate Plugin Testing at Scale
Use tools like curl, wp-cli, PHPStan, and regex scripts to mass-download, install, and scan plugins. Automation is key to testing hundreds of plugins efficiently.
6. Get Comfortable with Burp Suite
Burp is a must-have tool for intercepting and modifying HTTP traffic. Learn how to use it to find parameter tampering, missing CSRF nonces, and XSS entry points.
7. Focus on Plugins with 50k+ Installs
Especially if submitting to Wordfence bug bounty, where only popular plugins qualify for payouts. Prioritize plugins with large user bases for higher bounty potential.
8. Write Clear Proof of Concept Reports
Your report should include steps to reproduce, impact, and a working payload. A clean write-up increases your chance of being rewarded and credited with a CVE.
9. Follow Disclosure Rules Strictly
Submit bugs privately through Wordfence or Patchstack. Don’t tweet or blog about the bug until it’s patched.
10. Track Your Progress and Build a Portfolio
Use GitHub or a blog to share your public CVEs, write-ups, and tools (once disclosed). Patchstack also offers public researcher profiles to showcase your work.
How to Get Started Quickly
Step 1 – Register for Bug Bounty
- Take 1 minute to register a researcher account at Wordfence.
Step 2 – Prepare WordPress
Windows Guide
MacOS Guide
Step 3 – Download Required Files
Setup & Exploit Demo
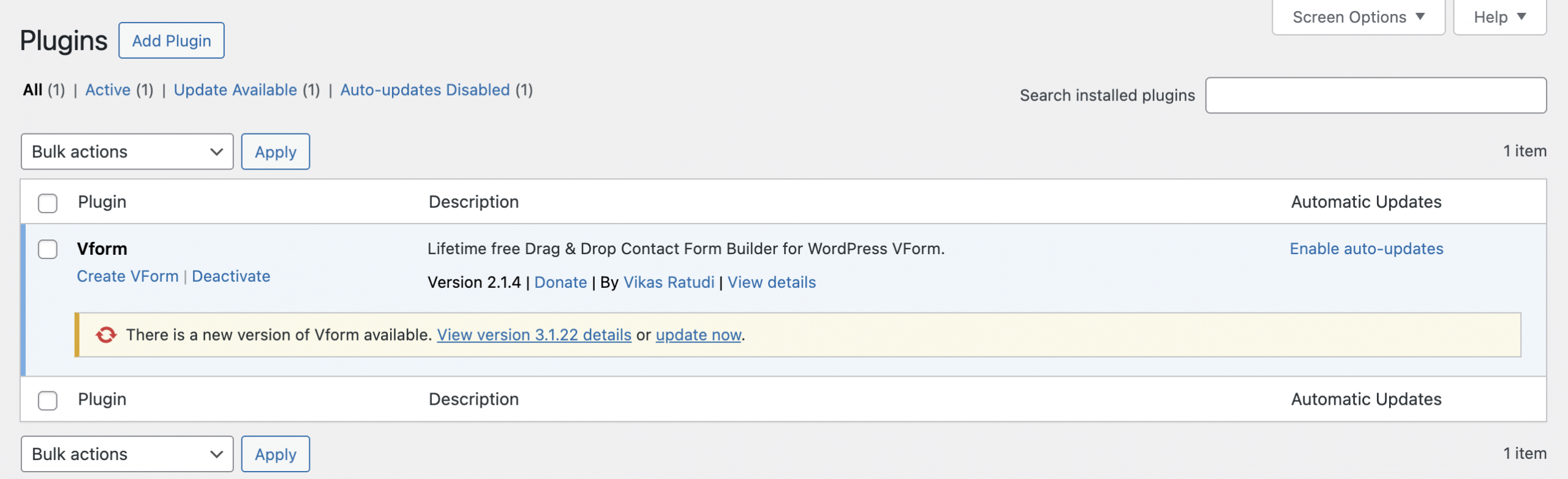
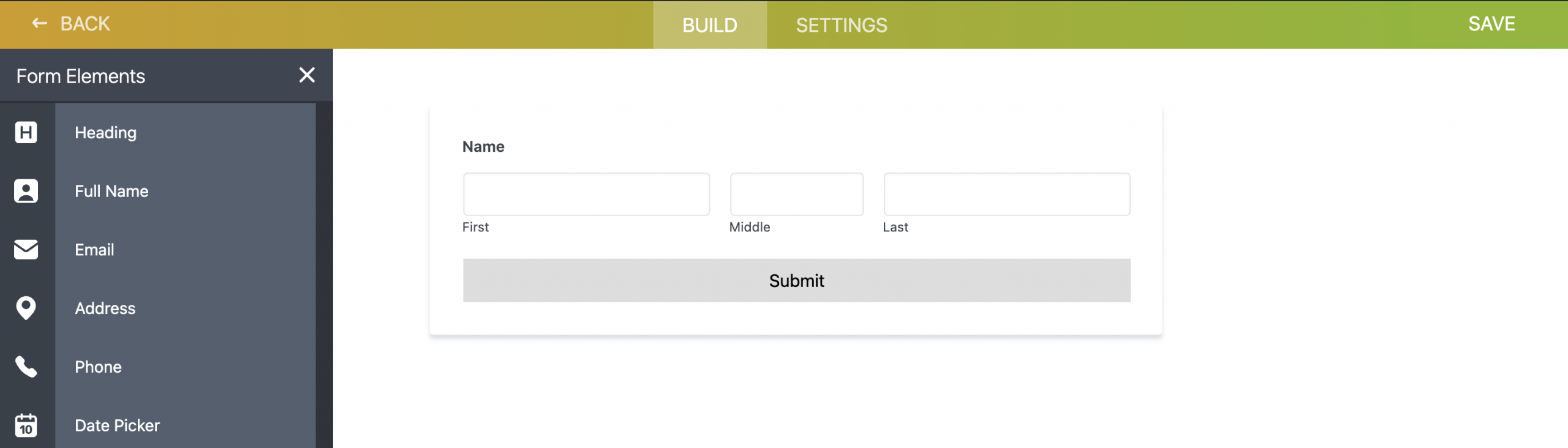
Step 1 – Install the Plugin
Step 2 – Create a Form
-
Go to Dashboard → Vform.
-
Click “Add New” to create a new form.
-
Click “Add Form Element” on the top left.
-
Select “Full Name” to add the input field.
-
Click “Submit” to add the submit button.
-
Click “Save” (top right), then return to the main Vform screen.
Step 3 – Add Form to the Page
-
On any page, insert the shortcode:
[vform id="1"]
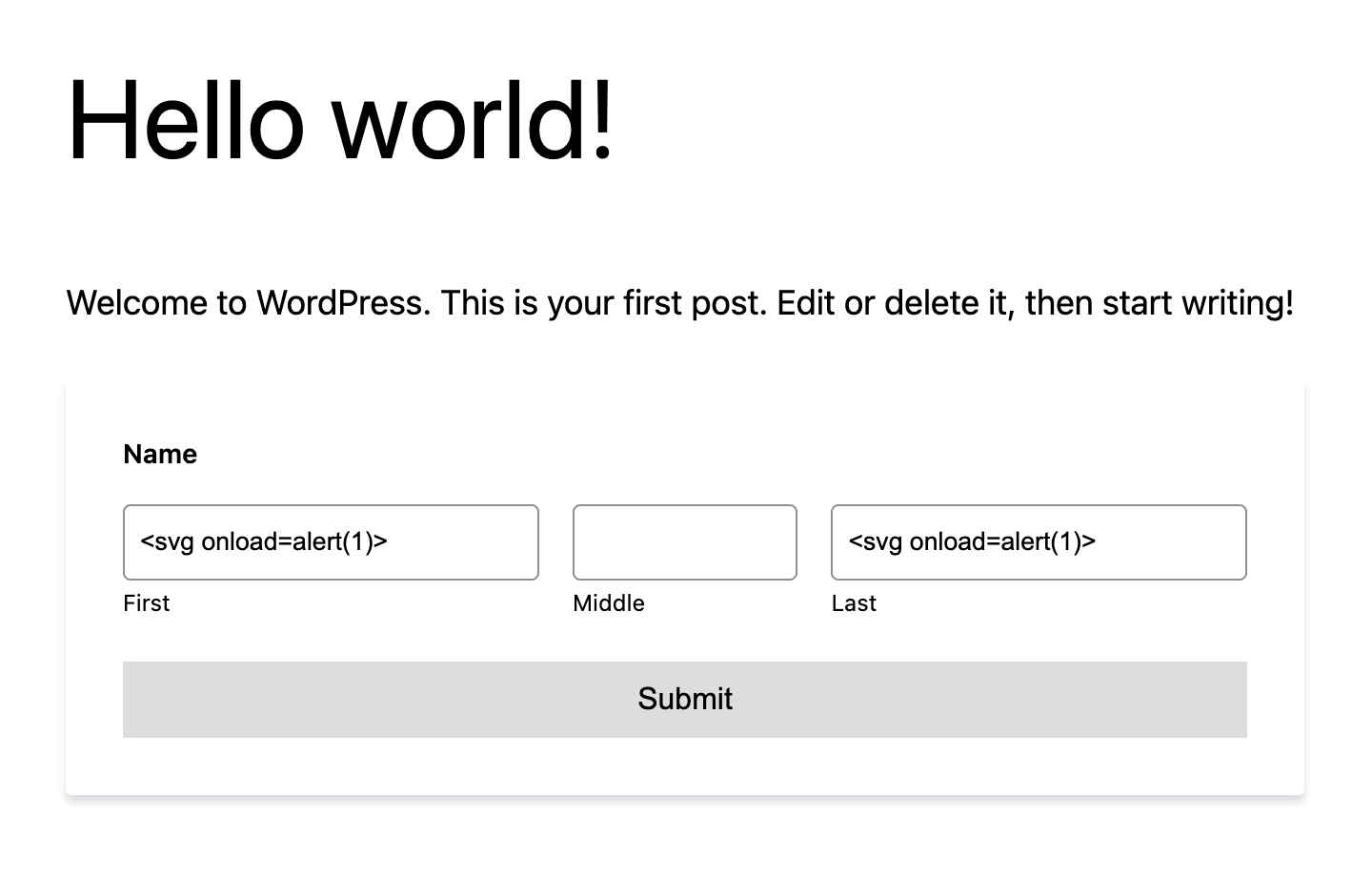
Step 4 – Submit XSS Payload
-
Open that page and enter the following payload in the First name field: <svg onload=alert(1)>
- Click Submit.
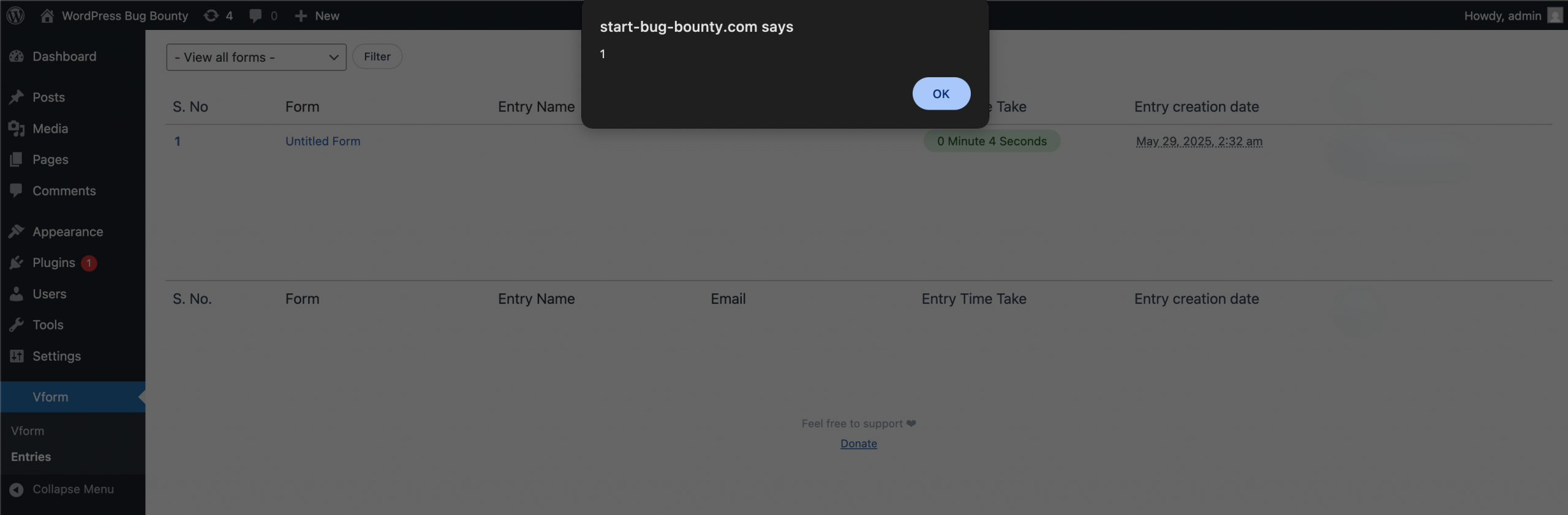
Step 5 – Validate Execution
-
Now go to Dashboard → Vform → Entries.
-
You’ll see the XSS payload executes in the admin’s browser — confirming stored XSS without authentication.
The Key – Testing WordPress Plugins at Scale
Why Scale Matters
-
Manual testing = slow, limited results
-
Scalable automation = higher chances of discovering WordPress plugin vulnerabilities before others
-
Essential for reporting multiple bugs to Wordfence, Patchstack, and other bounty programs
Testing at scale requires full automation of each step in the process. Manually testing hundreds of plugins is neither practical nor efficient, so automating the workflow is essential. Here’s how you can approach it:
1. Mass Download Plugins
Use tools like curl, wget, or even custom browser extensions to bulk-download plugin ZIP files from trusted repositories. You can also scrape plugin lists or leverage APIs provided by platforms like WordPress.
2. Filter Plugins for Vulnerabilities
Once you’ve downloaded the plugins, filter out ones that seem potentially vulnerable or have “code smells.” Use static analysis tools such as:
- Regex: Identify suspicious patterns in code (e.g., unescaped inputs, eval functions, SQL queries).
- Snyk: Check for known vulnerabilities in plugin dependencies.
- PHPStan: Perform static analysis to catch issues in PHP code.
3. Mass Install Plugins
Automate the installation process using tools like Bash, Python, or PowerShell scripts to deploy plugins to test environments. WordPress CLI (wp-cli) can also be incredibly useful for batch installation and activation of plugins.
4. Test for Vulnerabilities in Batches
Once installed, run your testing processes in batches:
- Observe how the plugins execute.
- Focus on areas prone to vulnerabilities, such as file uploads, JavaScript execution, or database queries.
- Utilize tools like Burp Suite or OWASP ZAP to identify vulnerabilities dynamically.
5. Erase the Testing Environment
After each batch, completely wipe the test environment. Plugins, especially low-quality ones, can leave behind database changes, temporary files, or even malicious scripts. Use tools like Docker containers, virtual machines, or cloud snapshots to reset the environment quickly and reliably.
6. Automate Everything
Automate as much of this process as possible. Use scripts and tools tailored to your setup:
- Bash for Linux environments.
- Python for its libraries and versatility.
- PowerShell for Windows-based workflows.
Every step—downloading, filtering, installing, testing, and cleaning up—should be automated. Without automation, scaling the process is impossible.
Tools and Techniques Recap:
- Mass Download:
curl, APIs, browser extensions. - Filtering: Regex, Snyk, PHPStan.
- Installation: Bash, Python, PowerShell,
wp-cli. - Testing: Burp Suite, OWASP ZAP, automated scanners.
- Environment Cleanup: Docker, cloud snapshots, or scripted reset processes.
Remember: automation is key. Without it, testing at scale isn’t achievable. Treat Bash, Python, and PowerShell as your best friends and optimize your workflow at every stage.
Most Frequent Questions
How much can I earn from WordPress bug bounty programs?
WordPress bounty earnings vary based on the bug’s severity and the program:
Type |
Typical Range |
|---|---|
| XSS / CSRF (Low impact) | $80 – $300 |
| Auth bypass / SQLi | $500 – $1,200 |
| RCE / Privilege Escalation | $1,000 – $3,000+ |
| Patchstack Monthly Bonus | $500 – $2,000+ (top rank) |
Some researchers earn $500–$2,000/month through consistent submissions. Others report lifetime earnings over $20K across platforms.
How does the Wordfence bug bounty program work?
The Wordfence bug bounty program pays you for reporting vulnerabilities in plugins/themes with 50,000+ active installs.
-
Payouts range from $80 to $1,600+ depending on severity and plugin popularity.
-
Critical bugs (RCE, file upload, privilege escalation) earn the most.
-
You get CVE assignment and are publicly credited.
-
No leaderboard—every valid report earns a reward.
Ideal for researchers looking to scale vulnerability discovery across top WordPress plugins and earn consistently.
What are the best WordPress bug bounty programs to join?
Here are the top programs:
Program |
Best For |
Link |
|---|---|---|
| Wordfence | High payouts, plugin focus | Visit |
| Patchstack | Beginners, community support | Visit |
| WordPress | Core CMS & .org infrastructure | Visit |
| Automattic | Jetpack, WooCommerce, WordPress.com | Visit |
What is a WordPress bug bounty program?
A WordPress bug bounty program rewards ethical hackers and security researchers for finding and responsibly reporting vulnerabilities in the WordPress ecosystem—including plugins, themes, and core infrastructure.
Instead of exploiting these flaws, researchers submit reports to platforms like:
These programs aim to improve WordPress security while offering rewards like CVEs (Common Vulnerabilities and Exposures), public recognition, and cash payouts ranging from $80 to over $3,000 per vulnerability. It’s a structured way to build cybersecurity skills and get paid for doing so.
How does the Patchstack bug bounty program work?
Patchstack’s bug bounty is open to all plugins and themes, regardless of install count, and designed to be beginner-friendly.
-
Submissions earn you CVE credits + XP points
-
Top researchers each month split a $8,800+ prize pool
-
Zero-day bugs or high-impact issues can earn $1,000–$14,000
-
Great for learning, networking, and building a security reputation
Patchstack runs a public researcher leaderboard, publishes vulnerability write-ups, and promotes contributors in security roundups and whitepapers.
Does WordPress have an official bug bounty program?
Yes. The WordPress Security Team operates a bounty program via HackerOne, focused on:
-
WordPress Core
-
.org infrastructure (e.g., plugin repository, WordCamp.org)
Rewards vary based on impact, ranging from acknowledgment to cash bounties for critical bugs.
Important: For Jetpack, WooCommerce, or WordPress.com-related bugs, use the Automattic HackerOne Program.
What types of vulnerabilities are common in WordPress plugins?
Most bounty-eligible plugin bugs fall into these categories:
-
XSS (Cross-Site Scripting) – Injected scripts via input fields or settings
-
CSRF (Cross-Site Request Forgery) – Triggers changes through admin trickery
-
SQL Injection – Manipulating database queries
-
File Upload / RCE – Uploading or executing malicious files
-
Privilege Escalation – Gaining unauthorized admin access
XSS is by far the most frequent and is often the best starting point for beginners. For examples, check:
How do I responsibly report a WordPress vulnerability?
Responsible disclosure means submitting your bug privately and professionally through one of these options:
If the plugin author is reachable and there’s no bounty program, you can also email them directly.
🛑 Never publish or post the vulnerability before a patch is released.
✅ Include reproduction steps, proof-of-concept, impact summary, and affected versions.
![Insert VForm shortcode into WordPress page for XSS lab test Shortcode block with [vform id="1"] inserted into a WordPress page during bug bounty setup](https://artempolynko.com/wp-content/uploads/2025/05/wordpress-bug-bounty-vform-shortcode.png)